In a new development in the cybersecurity landscape, researchers are witnessing a significant upsurge in phishing attacks that are cunningly exploiting the Google Accelerated Mobile Pages (AMP) service. Google AMP is an open-source HTML framework co-developed by Google and 30 partners with the primary goal of accelerating the loading of web content on mobile devices, offering a more seamless user experience.
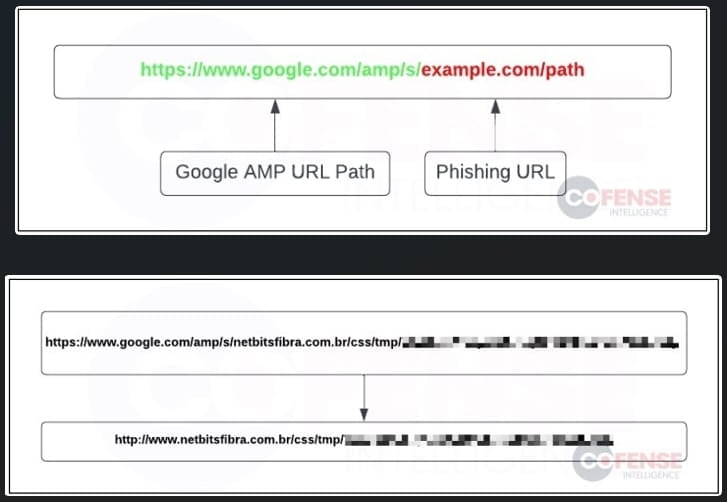
In these increasingly sophisticated phishing attacks, threat actors embed Google AMP URLs within phishing emails. The strategy behind this tactic is quite clever; by using Google AMP URLs, the attackers circumvent email protection systems that typically rely on reputation-based filters. Given Google's positive reputation, these systems do not flag messages containing Google AMP URLs as malicious or suspicious.
These Google AMP URLs act as a redirect mechanism to malevolent phishing sites. The additional redirection step introduced by the URL obscures the analysis of the threat, making it even more challenging for cybersecurity systems to identify and mitigate the threat promptly.
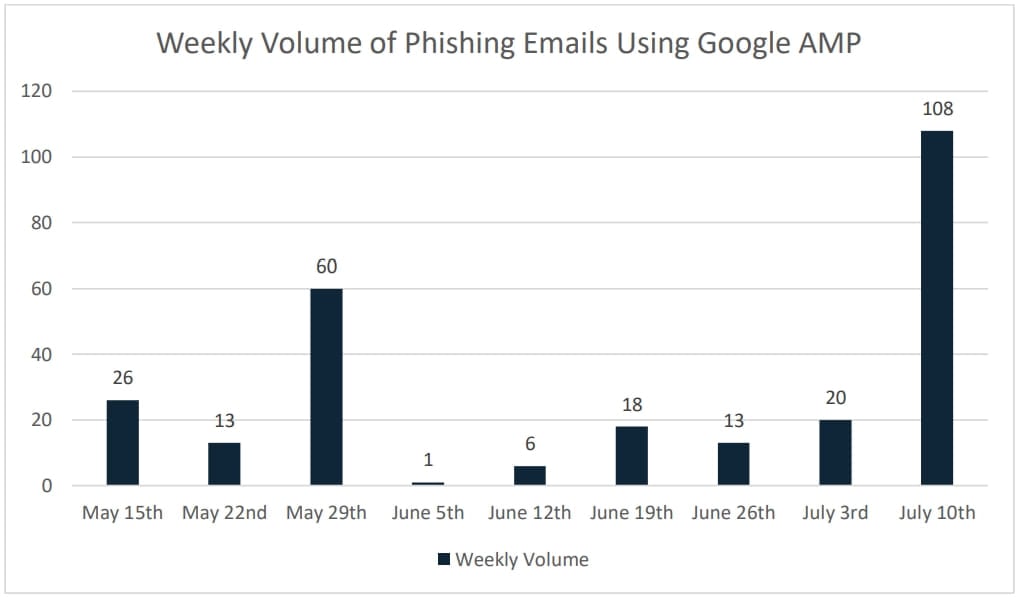
Cofense, a prominent company specializing in anti-phishing protection, has recently reported data indicating a steep rise in AMP-based phishing attacks, particularly from mid-July onwards. This pattern may suggest a wider adoption of the method by threat actors. The company's report details that about 77% of these deceptive Google AMP URLs were hosted on google.com, while 23% were hosted on google.co.uk.
However, tackling these threats poses a significant challenge, as it risks disrupting the legitimate use of Google AMP. The "google.com/amp/s/" path, a common element in these attacks, is widely used for genuine purposes, and blocking it could lead to unintentional service disruptions. A potential solution could involve flagging URLs that follow this pattern, warning email recipients of the potential threat, and encouraging them to exercise caution.
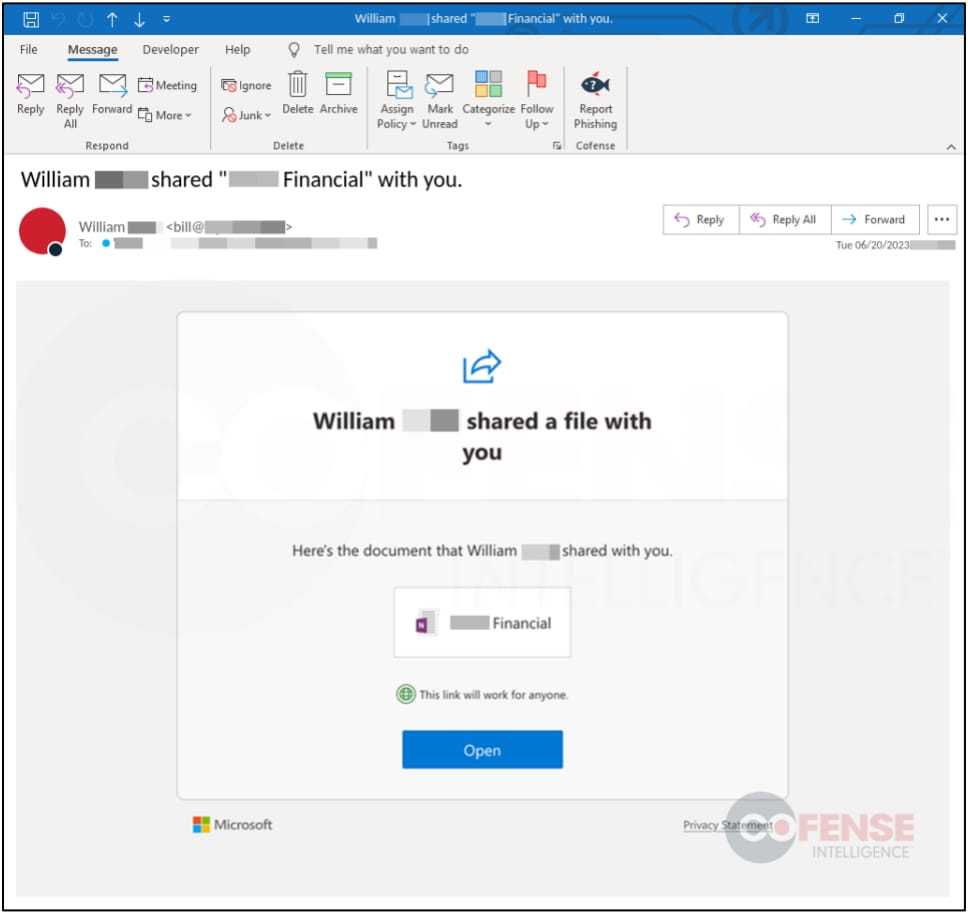
It's worth noting that the threat actors conducting these phishing attacks have adopted a variety of stealth techniques to increase their evasion capabilities and improve their attack success rates. Some of these methods include employing image-based HTML emails, which can effectively confound text scanners that typically search for common phishing terms in the email content.
Additionally, in some instances, the attackers add another layer of redirection by misusing a trusted Microsoft.com URL. This URL first redirects the victims to a Google AMP domain before eventually leading them to the actual phishing site.

In a further move to elude detection, the attackers also take advantage of Cloudflare’s CAPTCHA service. This tool helps them block automated analysis of phishing pages by security bots, which are then prevented from accessing and scrutinizing these malicious pages.
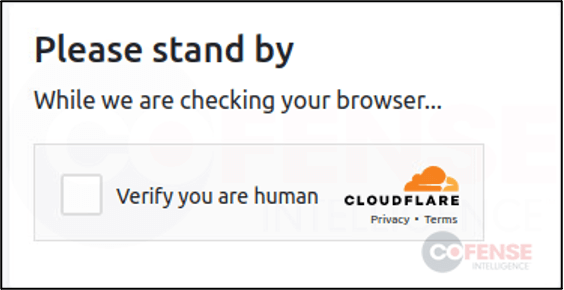
Cloudflare CAPTCHA pulled from Google AMP phishing campaign. (CoFense)
To summarize, modern-day phishing actors are utilizing a multi-layered approach involving various evasion techniques that significantly complicate the task of detecting and blocking these threats. These evolving tactics underscore the need for constant advancements in cybersecurity measures to keep pace with the ever-increasing sophistication of cyber threats.




